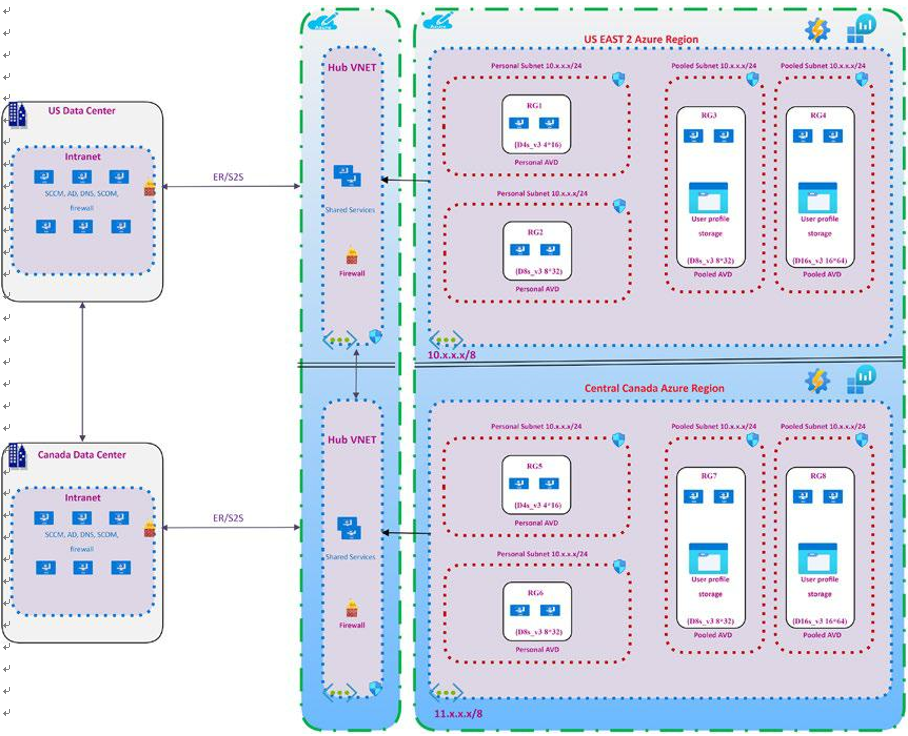
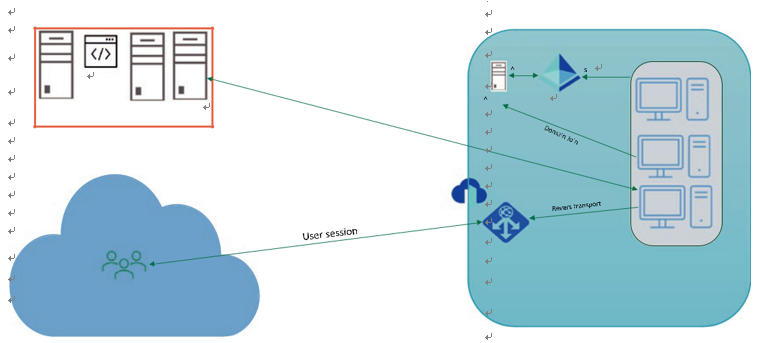
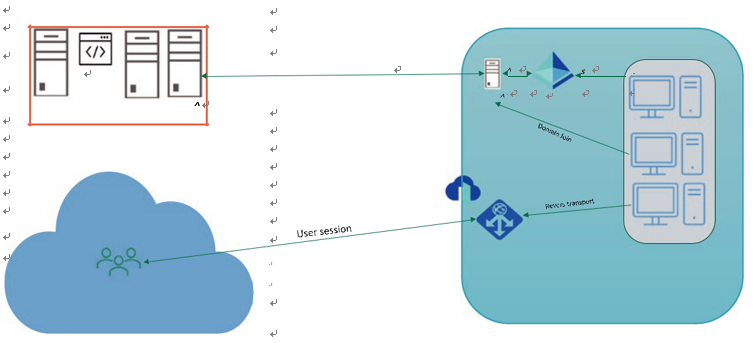
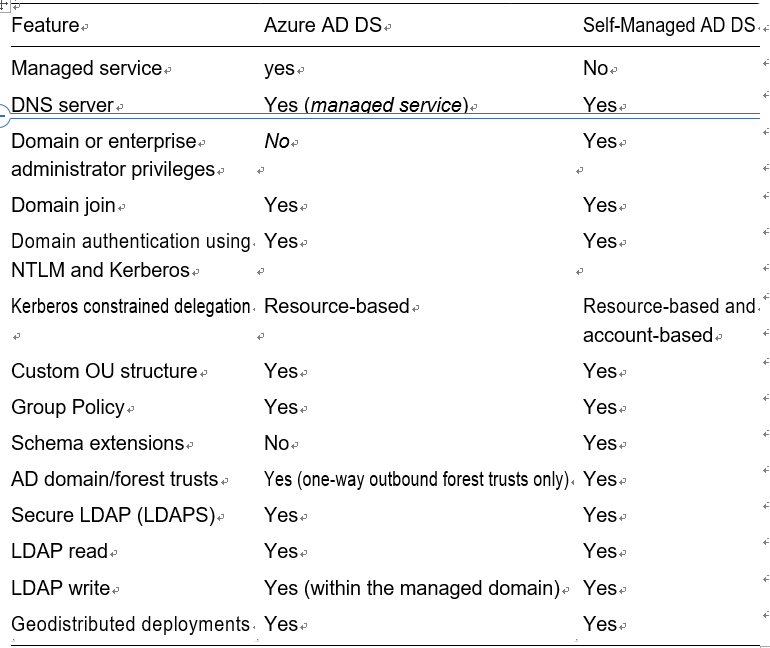
Important Consideration: Host Pool Outbound Access to the Internet
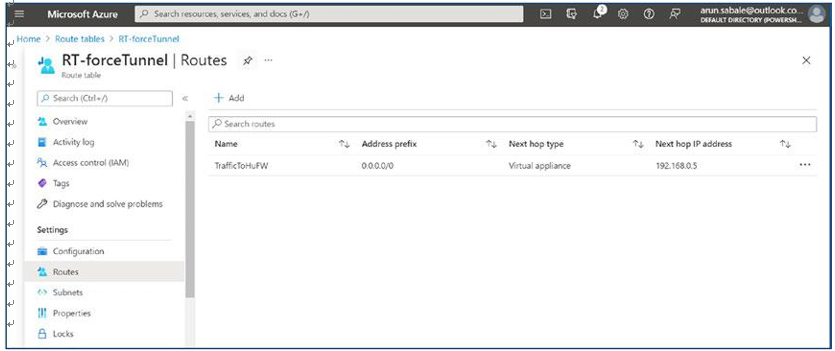
Based on your organization’s requirements, you may need to enable secure outbound Internet access for your end users. In instances where the list of allowed destinations is well-defined (for instance, Microsoft 365 access), you can use Azure Firewall applications and network rules to configure the required access. This routes end-user traffic directly to the Internet for the best performance.
If you want to filter outbound user Internet traffic using an existing on-premises secure web gateway, you can configure web browsers or other applications running on the Azure Virtual Desktop host pool with an explicit proxy configuration. These proxy settings only influence your end-user Internet access, permitting the Azure Virtual Desktop platform outbound traffic directly via Azure Firewall.
Manage Azure Virtual Desktop Session Hosts by Using Azure Bastion
In this section you’ll learn about Azure Bastion.
Configure AVD Session Hosts Using Azure Bastion
Azure Bastion offers secure connectivity to all VMs in a virtual network in which it is provisioned. Utilizing Azure Bastion protects your virtual machines from exposing RDP/ SSH ports to the outside world, while still offering secure access utilizing RDP/SSH.
It is important to verify the criteria that you need to meet. Here is the list:
•\ You need a VNet with the Bastion host already installed. Make sure that you have set up an Azure Bastion host for the virtual network in which the VM is located. Once the Bastion service is provisioned and deployed in your virtual network, you can make use of it to connect to any VM in the virtual network.
•\ You need a Windows virtual machine in the virtual network.
•\ The required roles are as follows: Reader role on the virtual machine, Reader role on the NIC with the private IP address of the virtual machine, and Reader role on the Azure Bastion resource.
•\ To connect to the Windows VM, you must have the inbound port RDP (3389) open on your Windows VM.