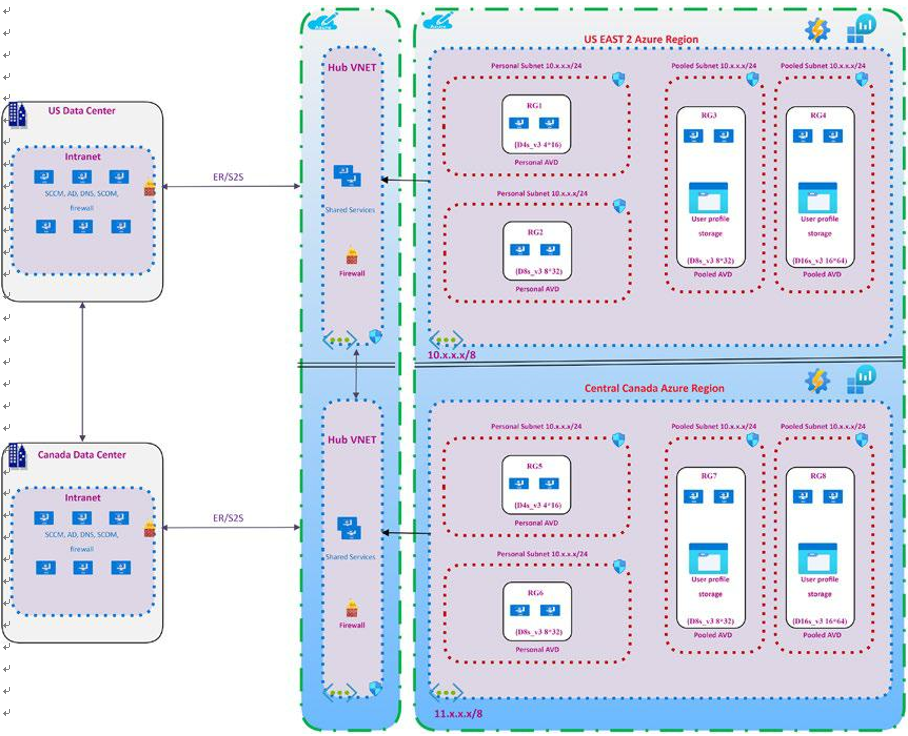
Recommended Storage Solution (Including Azure NetApp Files vs. Azure Files)
Azure Virtual Desktop performance is dependent on the storage type you are using, so it is important to select the appropriate storage for the operating system disk as well as the user profile data. Here are two different storages required for Azure Virtual Desktop:
•\ Operating system storage: For optimal performance, it is recommended that you use premium SSD storage for the Azure Virtual Desktop session host’s operating system disk for production workloads. The operating system disk size depends on the operating system and applications installed on the C: drive.
•\ User data storage
•\ Storage for personal desktop: A personal desktop is a persistent desktop, meaning the user will get the same desktop every time they log in to Azure Virtual Desktop. The user can store data on the local VM. Additional standard or premium storage can be attached to the personal Azure Virtual Desktop instance to store user data or install applications.
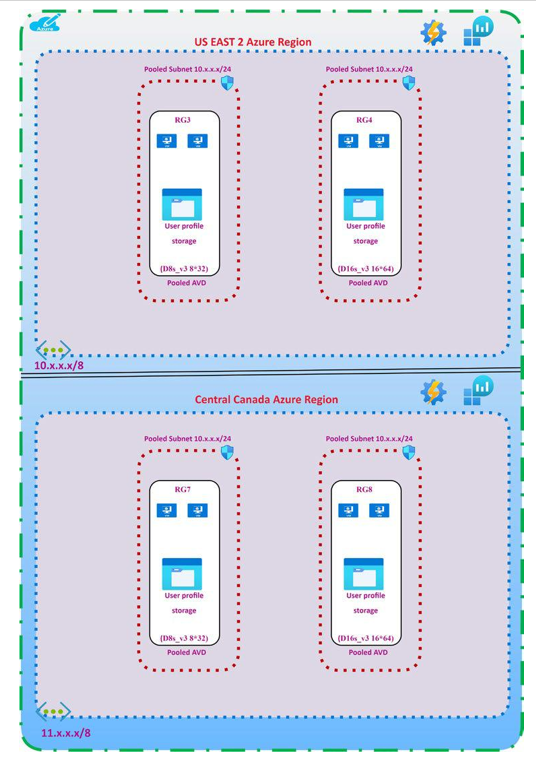
•\ Storage for pooled desktop user profile (pooled): Since pooled desktops are not persistent desktops, the user will not get the same VM every time they log in to Azure Virtual Desktop.
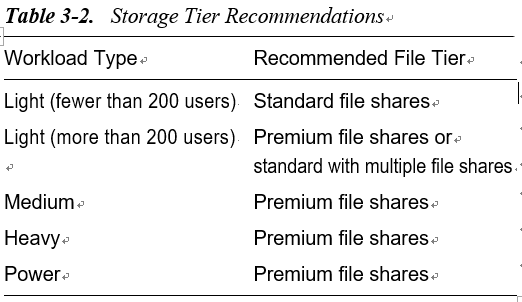
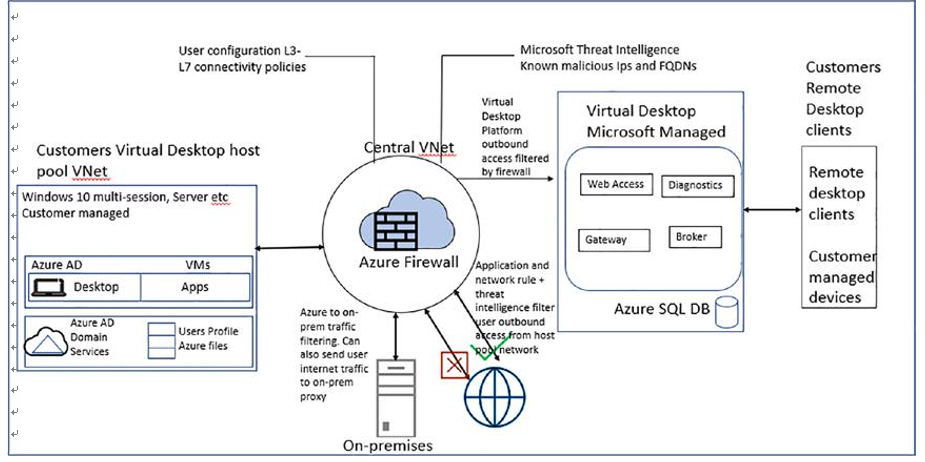
Therefore, the user profile must be stored on remote storage using FSLogix. Pooled Azure Virtual Desktop supports FSLogix, which helps to store user profiles on Azure Files as well as Azure NetApp Files. Both Azure Files and NetApp Files support ADDS authentication as well as secure access over a virtual network, and it is recommended that you restrict the profile storage to a specific virtual network with a private endpoint. You can use a storage domain join so authorized users can access storage and user profiles.
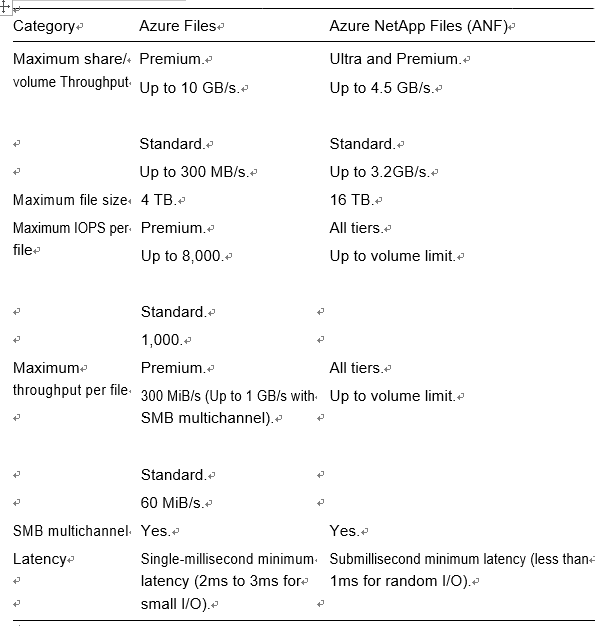
Table 3-1 compares the major differences between Azure Files and NetApp Files to help you make a decision.
Table 3-1. Differences Between Azure Files and NetApp Files
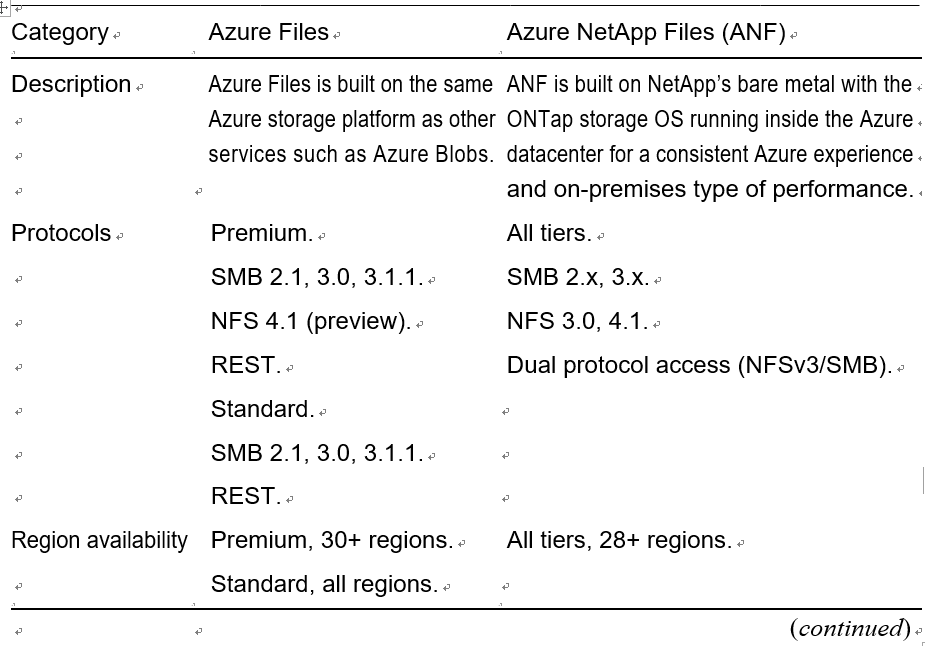
Table 3-1. (continued)

Table 3-1. (continued)
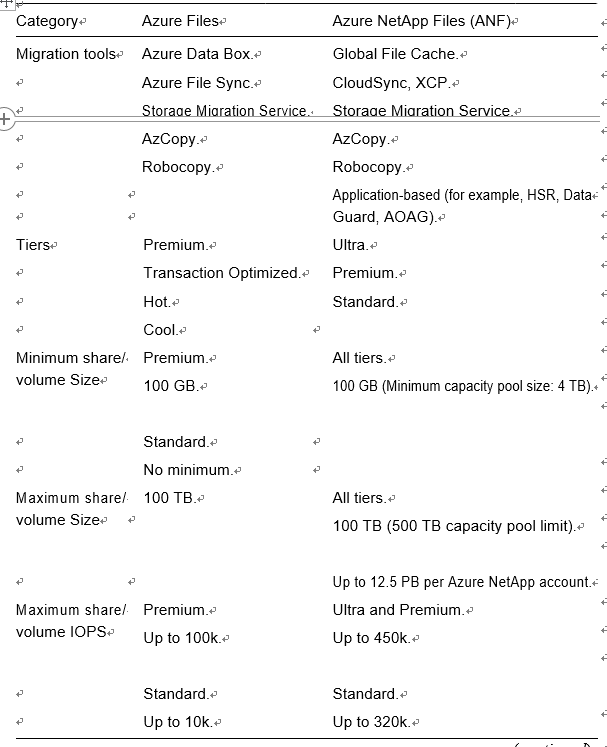
Table 3-1. (continued)